Azure Network EP4 – Network Security Group (NSG)

Azure-Network-EP4-Network-Security-Group-(NSG)
Hello Friends,
Let’s continue with Azure Virtual Network in this article. We have started a journey with Azure networking and this is the 3rd article on this series. If you have missed our last articles, please check in following links.
EP 1 – Basics of Azure Networking
EP 2 – Azure Virtual Network (VNet)
EP 3 – Subnet in Azure Network
Next Article: EP5 – Basics of Azure Application Gateway
In this article, we will discuss the Network Security Group (NSG).
As we know a Network Security Group (NSG) contains a list of security rules and Access Control List (ACL) that allow or deny network traffic to resources connected to Azure Virtual Networks (VNet).
An NSG is a firewall policy, defining a collection of inbound and outbound allow or deny rules for network traffic. We can enable network security group flow logs to analyze network traffic to and from resources that have an associated network security group.
NSG can be associated with subnet level or NIC level or both? Binding NSG to the individual VMs (by NIC) is powerful, but we may quickly lose control of the complexity of our deployment because it would be hard to track and maintain. So it is recommended to link NSG to the subnet level and reuse it across our VNETs and subnets. The best practice is to design our VNET architecture before and also according to our NSG requirement. Once we have designed our network topology, then need to think about the architecture of the boundaries we want to deploy. In the following figure, we can see the NSG requirement for our current requirement.
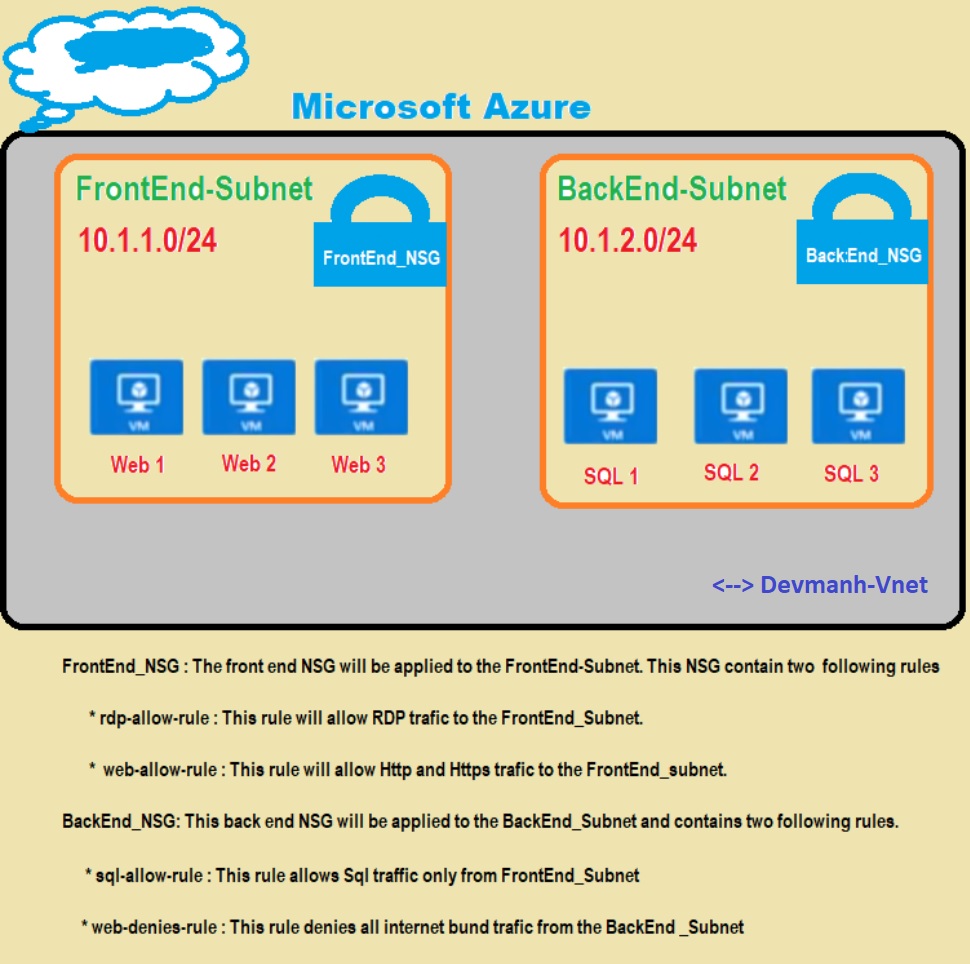
In our last article, we have created two Azure Subnets. Here we will create two different NSG for each of our subnets. Both NSG will have different security policies for inbound and outbound traffic. So let’s go through the following steps to create and configure two NSG for two subnets.
I. Create Network Security Group (NSG) Using Azure Portal
1. Connect to your Azure portal dashboard using your subscription account. If you don’t have any subscription, in that case you can get a trial Azure subscription with one-month of validity. Then you can connect to the Azure portal dashboard as shown in the following figure.

Figure 2: Azure – portal dashboard
2. On the left side menu of the screen, select Create a resource > and try to find Network Security Group from the azure marketplace as shown in the following figure and then click Create button to create a new NSG.
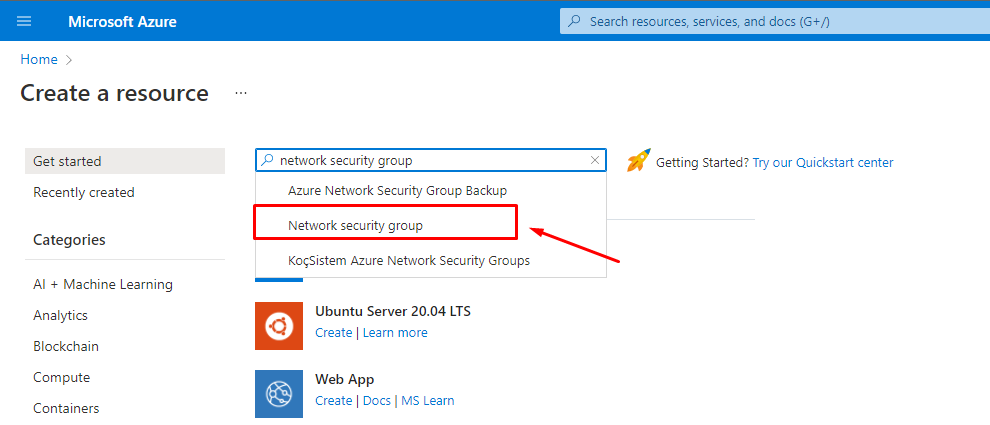
Figure 3: Azure – Find Network security group from Azure marketplace
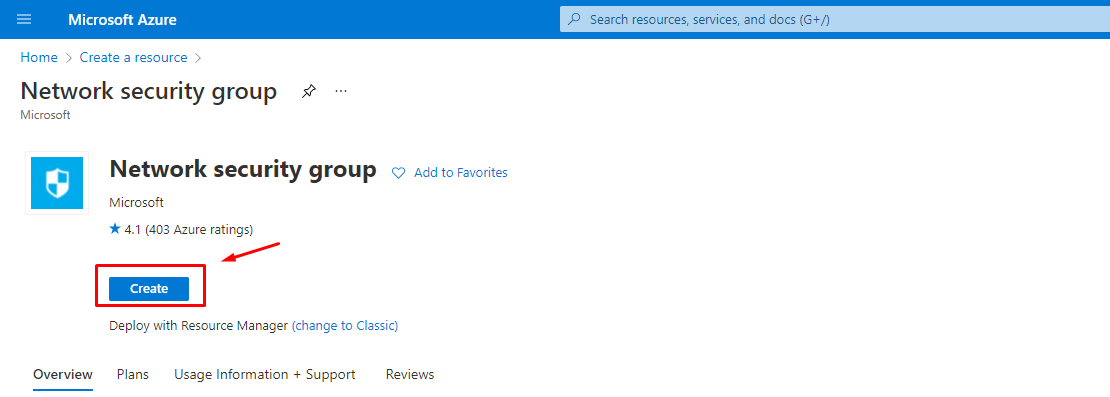
Figure 4: Azure – Create First NSG for Front End subnet
3. This will allow us to provide the required information for our first NSG as shown in the following figure and then click Create button to create the NSG.
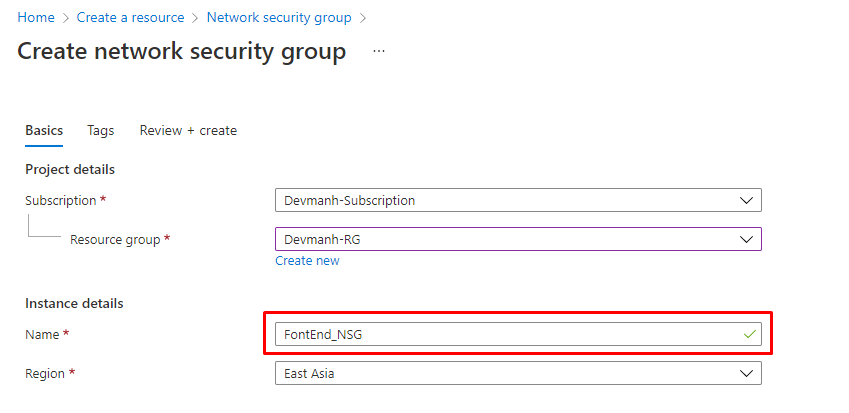
Figure 5: Azure – Create first NSG
4. Follow the above steps to create our second NSG as shown in the following figure.
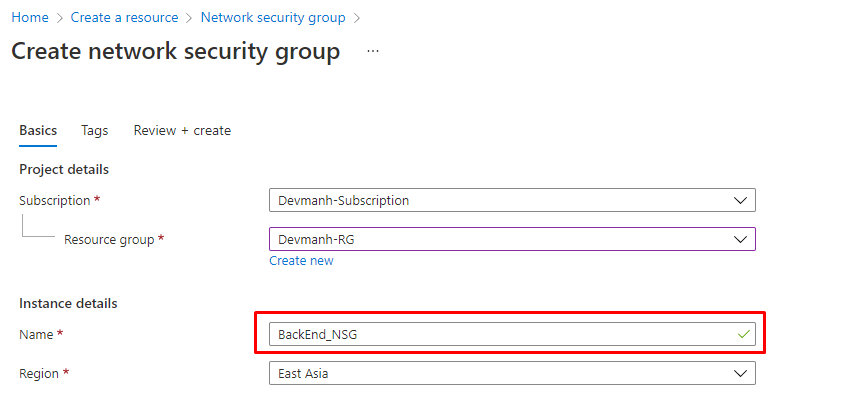
Figure 6: Azure – Create the second NSG
In the following figure, we can see that we have crated our two Network security groups. Now we need to add security policies ( both inbound and outbound traffics ) to both NSGs.
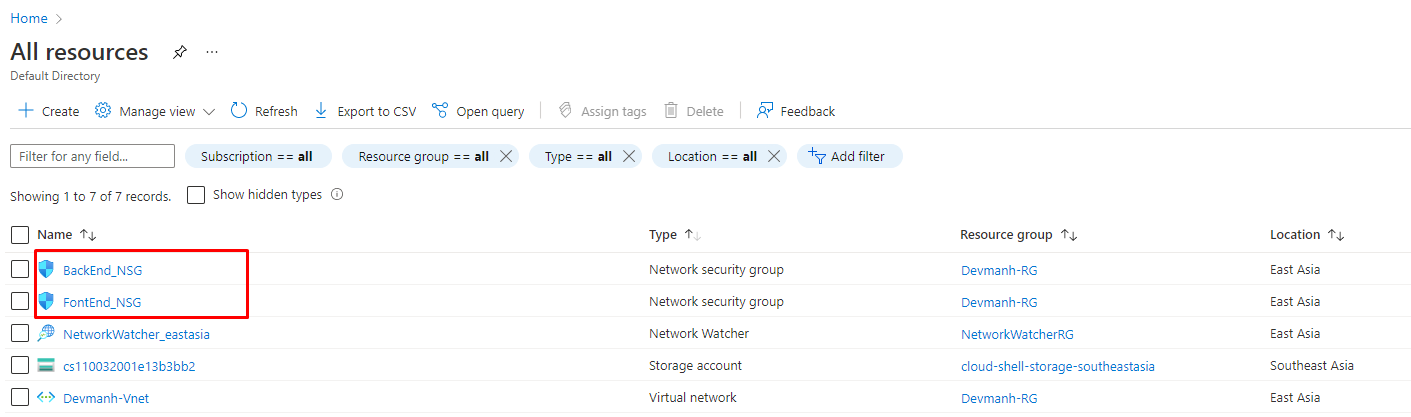
Figure 7: Azure Created two NSGs
we have created two NSGs, now we will move forward and add traffic rules to both Subnets as per the rule defined in Figure 1.
6. To add rules to both NSG, we need to open newly created NSG one by one. In the following figure, we can see, there are a few default rules added for both Inbound and Outbound traffics. For FrontEnd_NSG, we need to add two new rules as shown in the following figures.
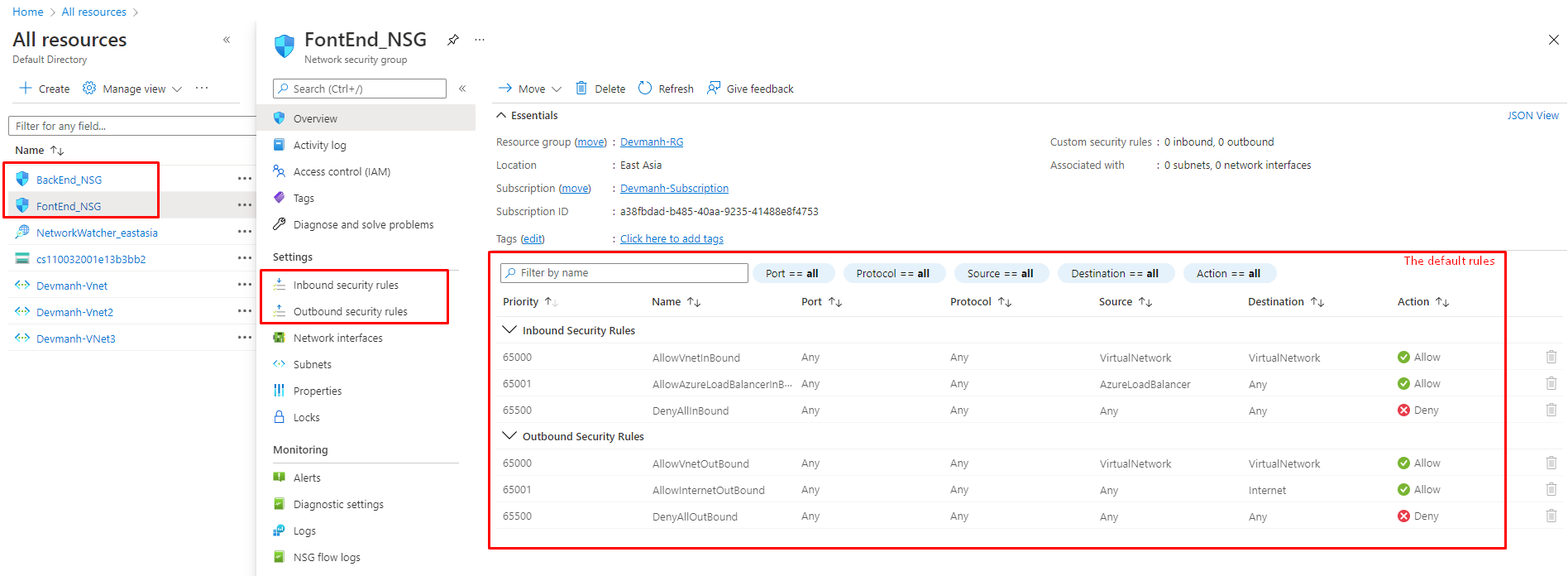
Figure 8: Azure – Default rules with newly created NSG
7. Select Inbound security rules and click the +Add button to add new rules as shown in the following figure.
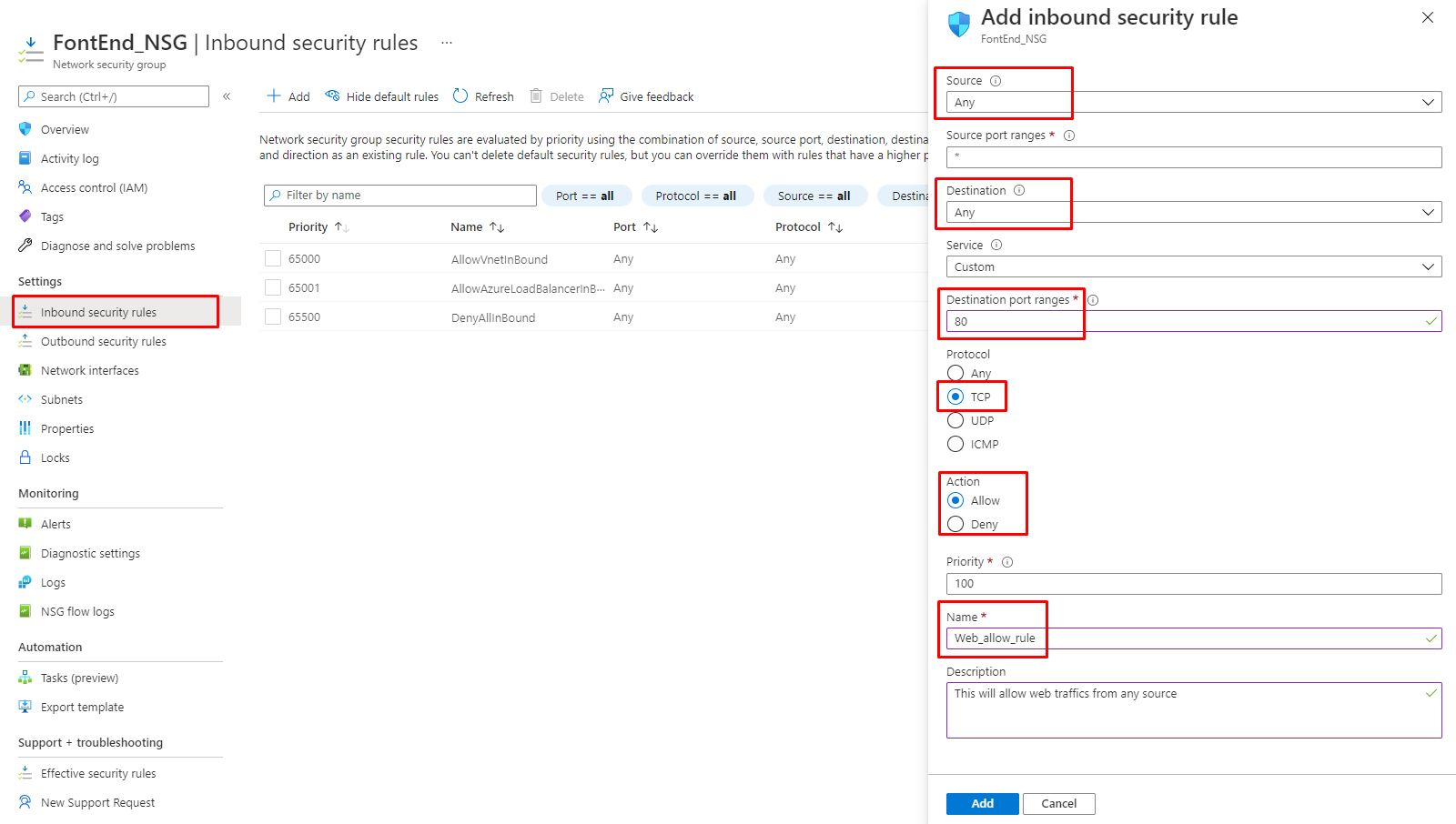
Figure 9: Azure – Adding a new web-allow rule to FrontEnd NSG
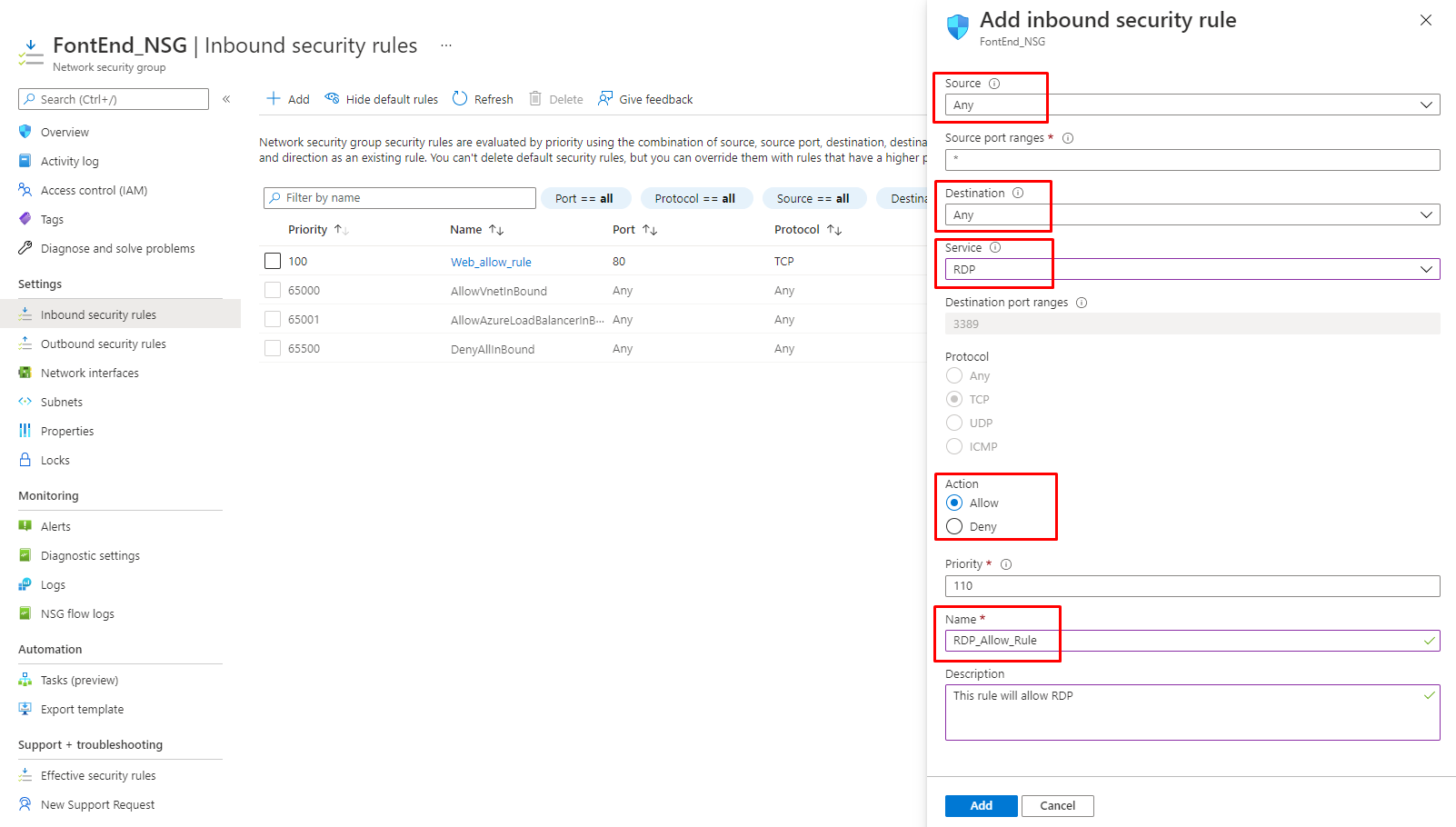
Figure 10: Azure – Adding new RDP-allow rule to FrontEnd NSG
8. We have added the required rules to FrontEnd NSG. Now let’s select BackEnd NSG to add one Inbound and one Outbound rule as shown following figure.
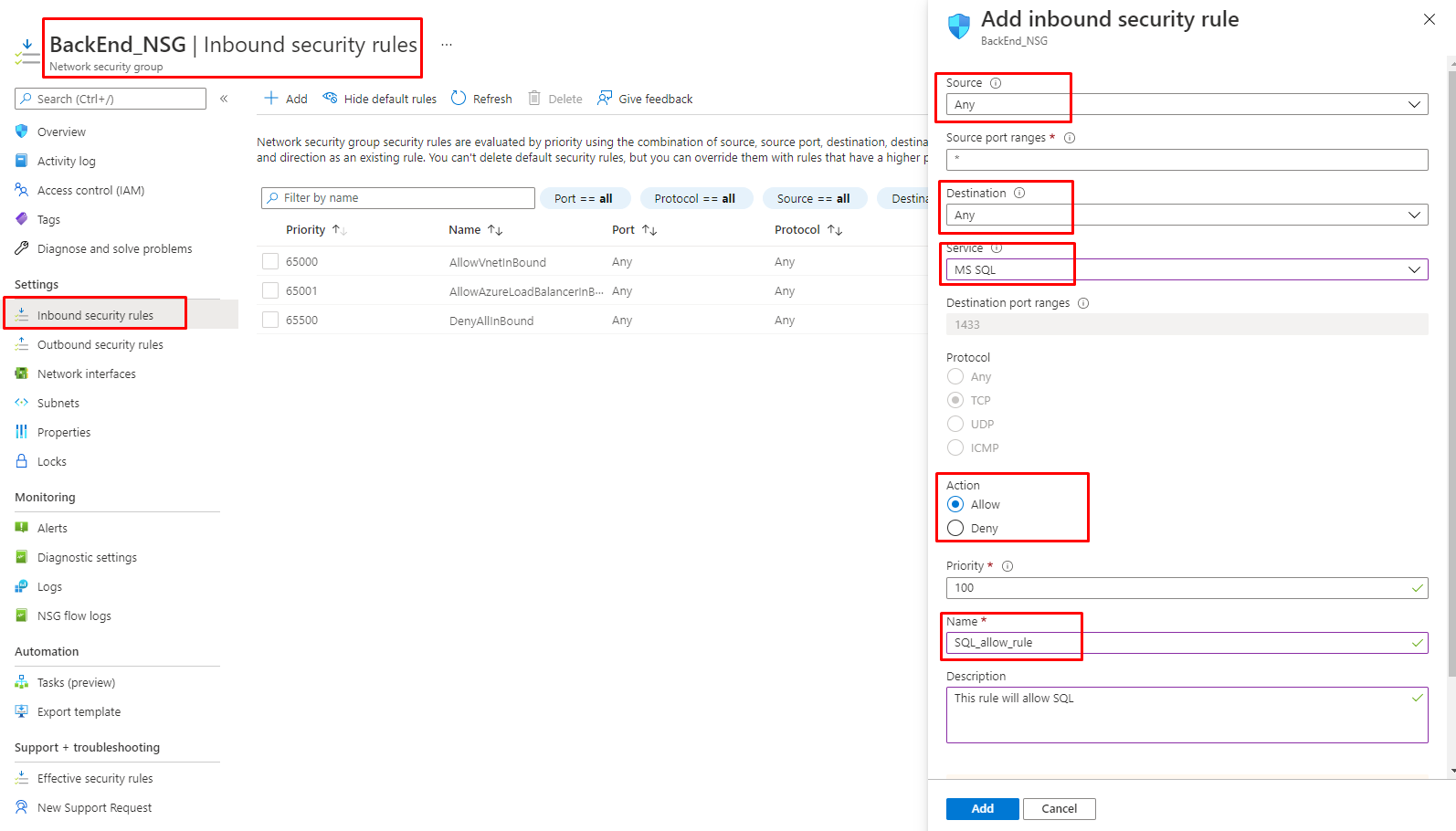
Figure 11: Azure – Adding Sql-allow rule to BackEnd NSG
9. After adding all Inbound rules, one outbound security rule needs to be configured to deny all internet access from BackEnd NSG. Let’s add the Outbound rule as shown in the following figure.
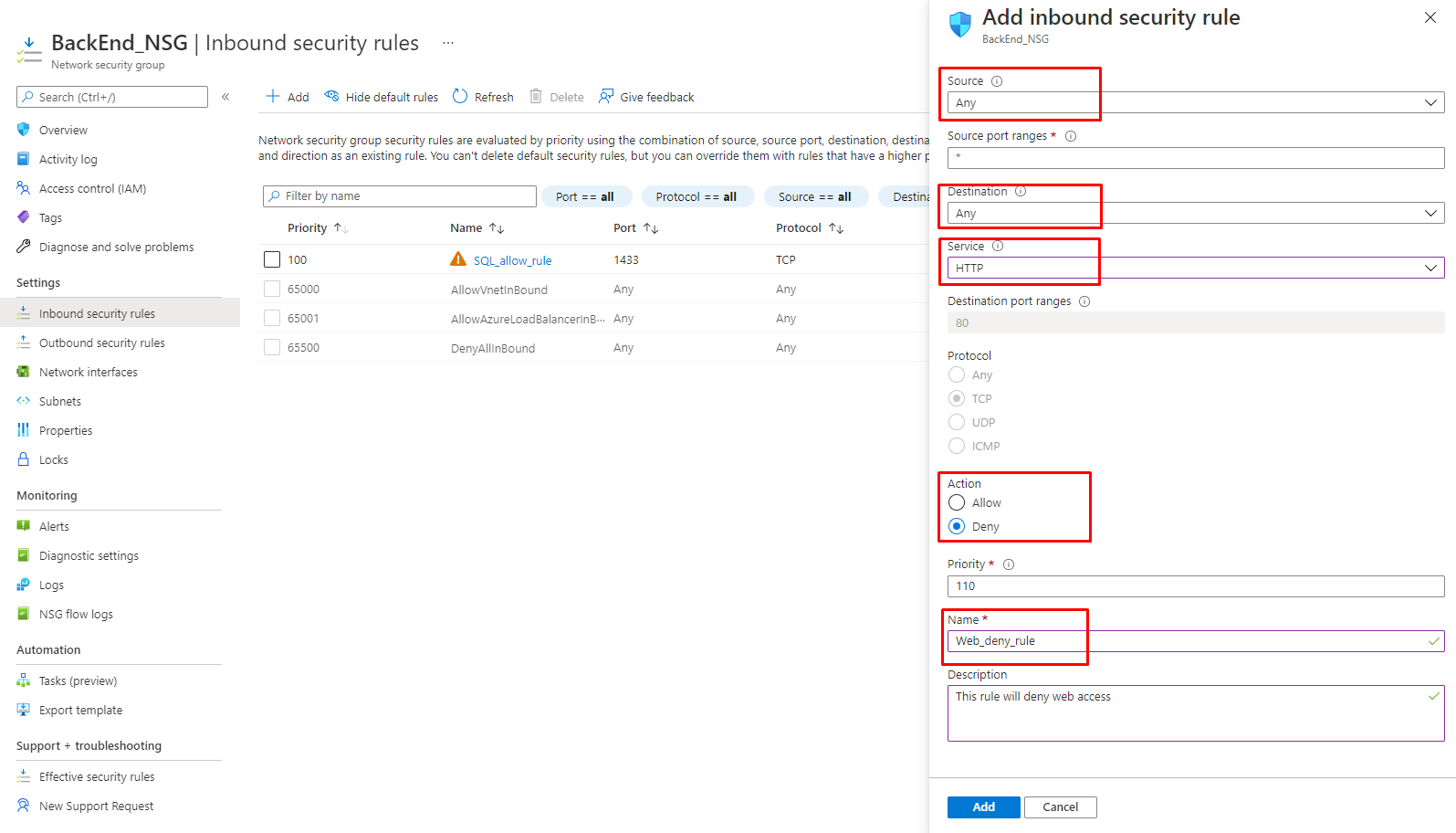
Figure 12: Azure – Adding Web-deny rule to BackEnd NSG
10. After configuring our NSGs with the required rules, the next step is to associate both NSGs to their respected Subnet. As shown in the following figure, open each Subnet and set its NSG property.
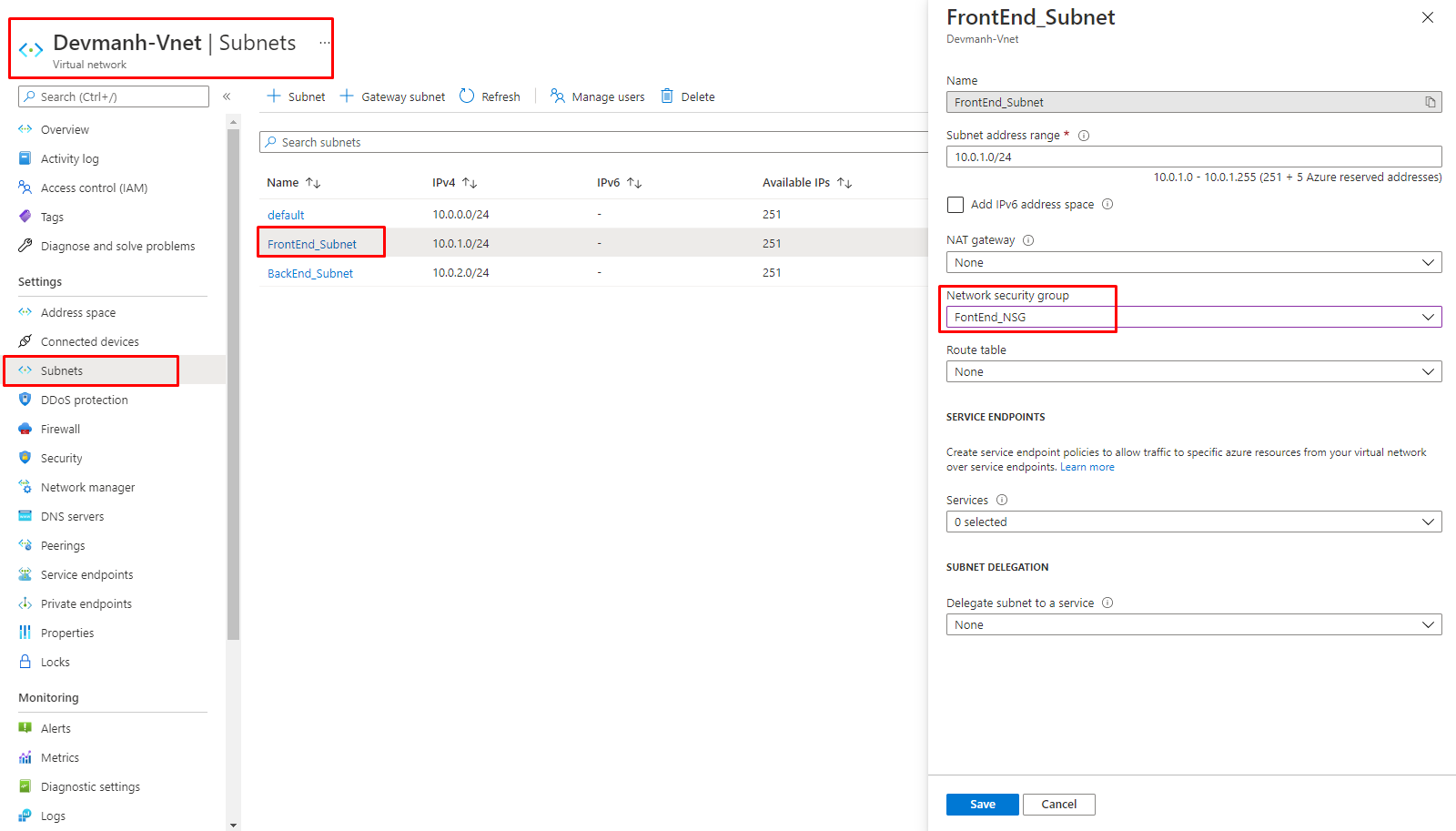
Figure 13: Azure – link FrontEnd_NSG to FrontEnd Subnet
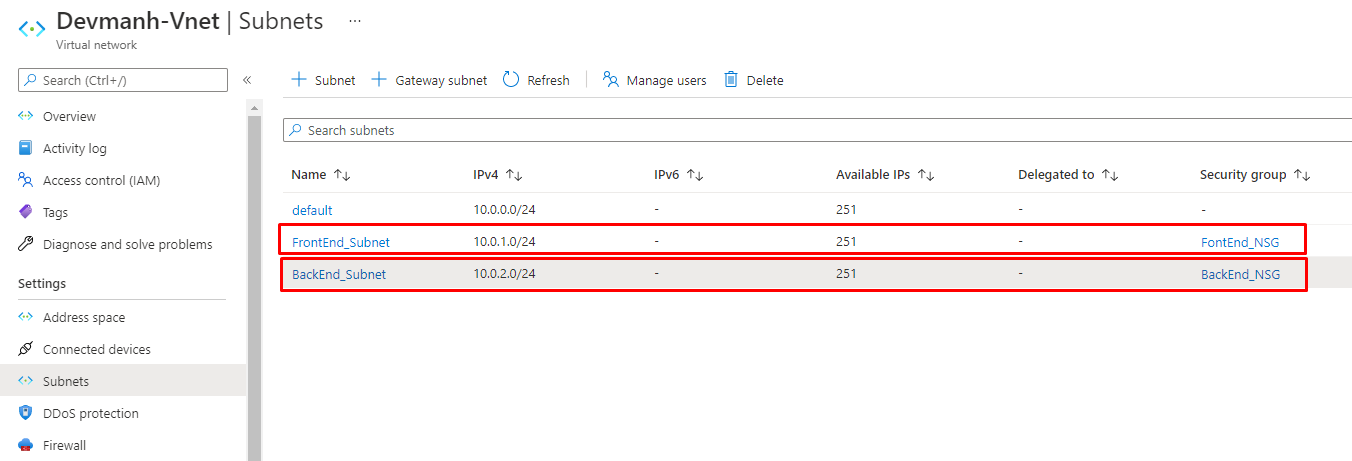
Figure 14: Azure – Linked proper NSG to Subnet
So far so good, now we have done with our NSG configurations. As we can see in our design, our web servers reside under FrontEnd Subnet and it is associated with FrontEnd_NSG. As per its Inbound rules, all servers under this NSG can be accessed through an RDP connection and web applications can be accessed through the internet.
In this design, we have configured BackEnd Subnet which is associated with BackEnd_NSG. We have an SQL server that resides under the BackEnd Subnet. As per its Inbound rule, the SQL database can be accessed from anywhere. Here SQL database can be accessible by web application deployed in servers, under FrontEnd Subnet. We have also configured an Outbound rule so that the internet can’t be accessible from any server residing under the BackEnd Subnet.
II, Create Network Security Group (NSG) Using CLI.
Syntax:
az network nsg create –name
–resource-group
[–location]
[–subscription]
[–tags]
Example:
az network nsg create -g Network_RG -n FrontEndNsg –tags super_secure no_80 no_3389
Add New Rule To Network Security Group (NSG) Using CLI :
Syntax:
az network nsg rule create –name –nsg-name –priority –resource-group [–access {Allow, Deny}] [–description] [–destination-address-prefixes] [–destination-asgs] [–destination-port-ranges] [–direction {Inbound, Outbound}] [–protocol {*, Tcp, Udp}] [–source-address-prefixes] [–source-asgs] [–source-port-ranges] [–subscription]
Example:
az network nsg rule create -g MyResourceGroup –nsg-name FrontEndNsg -n web-allow-rule –priority 100
Create Network Security Group (NSG) Using Power shell:
New-AzureRmNetworkSecurityGroup -Name BackEndNsg -ResourceGroupName Network_RG-Location eastasia
Add New Rule To Network Security Group (NSG) Using Power Shell:
$nsg=Get-AzureRmNetworkSecurityGroup -Name BackEndNsg -ResourceGroupName NEtwork_RG
$nsg | Add-AzureRmNetworkSecurityRuleConfig -Name sql-allow_rull -Description “Allow port for 1433” -Access Allow -Protocol Tcp -Direction Inbound ‑Priority 110 -SourceAddressPrefix Any -SourcePortRange 1433‑DestinationAddressPrefix * -DestinationPortRange *| Set-AzureRmNetworkSecurityGroup
I hope this article gives a basic understanding of Network Security Group (NSG) and how to configure traffic rules for an NSG. My next article of this series is EP5– Basics of Azure Application Gateway.
Thanks for reading 🙂
Keep reading, share your thoughts, experiences. Feel free to contact us to discuss more. If you have any suggestions/feedback/doubts, you are most welcome.
Stay tuned on the blog, will come up with more such articles.
Manas KJ




