Azure Network EP6 – Azure Application Gateway Features

Azure-Network-EP6-Azure-Application-Gateway-Features
Hello Friends,
Let’s continue with Azure Application Gateway in this article. In our last article, we have discussed a very important topic of Networking is Azure Application Gateway. In this article, we will discuss more Azure Application Gateway Features.
If you have missed our previous articles on networking, please check them in the following links.
EP1 – Basics of Azure Networking
EP2 – Azure Virtual Network (VNet)
EP3 – Subnet in Azure Network
EP4 – Network Security Group (NSG) in Azure
EP5 – Basics of Azure Application Gateway
Next Article: EP7 – Create An Application Gateway With URL-Based Routing Configuration- 1
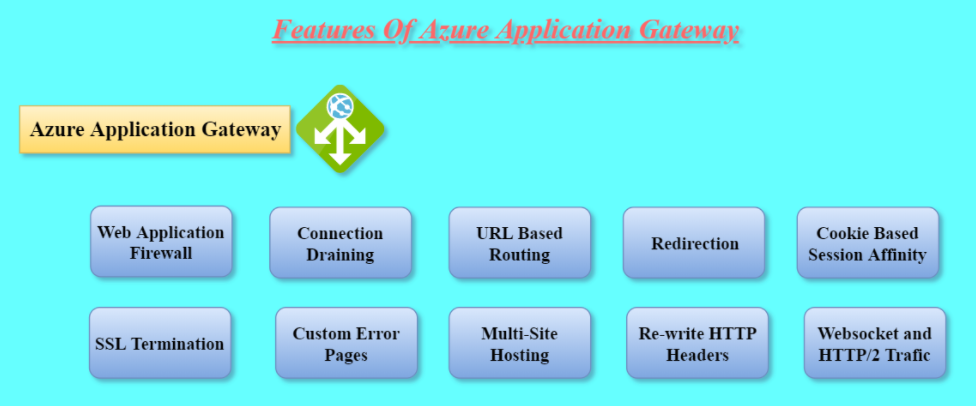
Azure Application Gateway is a popular service, because of its robust features. Let’s go through its most popular features.
Web Application Firewall (WAF) :
Web application firewall (WAF) is an application firewall for HTTP applications.
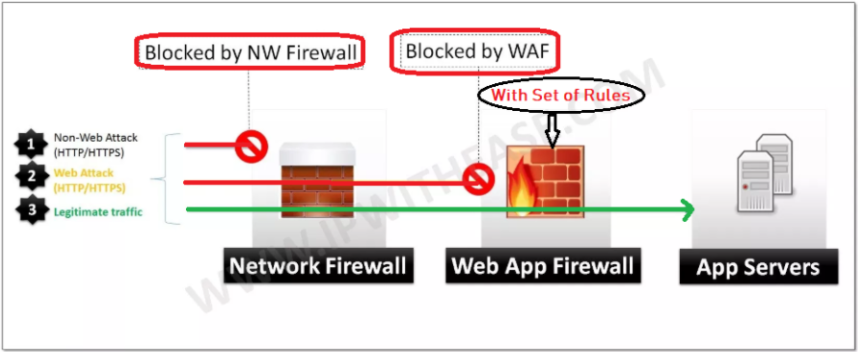
Figure 1: Azure – Web Application Firewall
- Web application firewall (WAF) is an application firewall for HTTP applications.
- WAF creates a set of rules designed to protect our website.
- Rule save applications, from common attacks, such as cross-site scripting (XSS), SQL injection, file inclusion, and security misconfigurations by inspecting HTTP/S traffics.
- WAF is capable to filter the content of specific web applications.
- Traditional F/W provides security from Layer 3 to layer 4 (IP, Ports in network layer).
- WAF provides security from layer 5 to layer 7 ( Http/s till application layer)
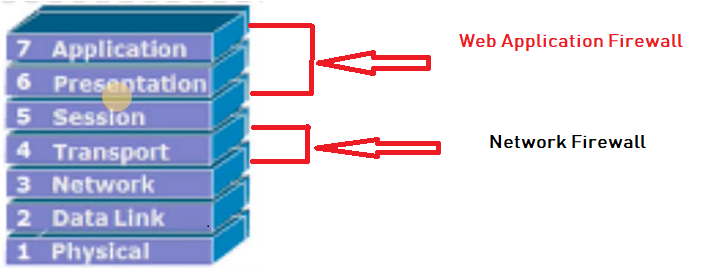
Figure 2: Azure – Firewall In 7 Layer
Connection Draining :
Application Gateway provides a Connection Draining feature to improve the availability of backend instances. This feature maintains the backend pool instances. Like, if a back-end instance fails health checks, the connection draining feature will not send any new requests to the unhealthy instance and remove the instance from the back-end pool and keep checking the health report for removed instances till received a good health report. It added back the removed instance to the back-end pool once it get ready with good health.
We can perform maintenance or replacement of back-end instances without impacting our customers’ experience. This feature is also helping to scale up the instances as per the requirement.
URL Based Routing :
A URL Path-Based Routing allows the application gateway to route our traffic to back-end server pools based on the URL Paths of the request. Due to this feature, the routing of the traffic to its destination is very accurate.
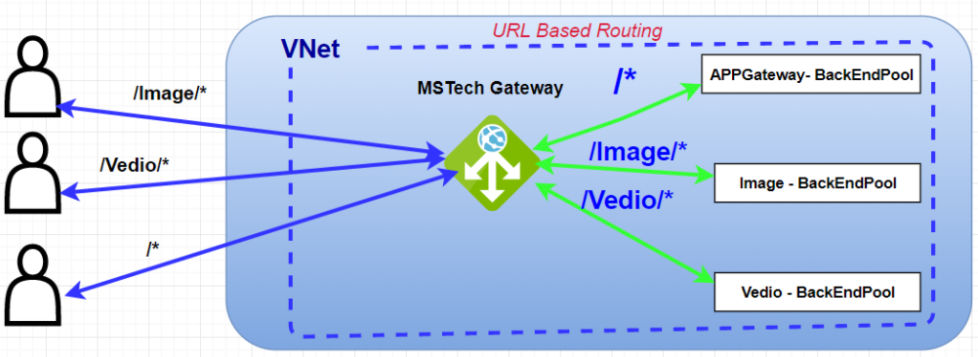
Figure 3: Azure AG – URL Based Routing
As in the above figure, there are three different backend pools to serve requests from the client. We need to configure a path-based routing rule to achieve URL-based routing. Set the Name, Path, Backend Pool, and HTTP setting at the time of rule configuration. Once we have done with the rule configuration we are ready to go and all paths will redirect to accurate backend pools.
For example requests for http://MSTechs.com/video/* are routed to Video-BackEndpool , and http:// MSTechs .com/images/* are routed to Image-BackEndpool. APPGateway-BackEndpool is selected if none of the path patterns match.
Redirection :
Redirection is a common feature of the application gateway. It supports automatic redirection from HTTP to HTTPS and vice-verse, so all the communication between application and user will be on an encrypted path. This feature also supports redirecting from any port to any other port based on the defined rules. It has the ability to redirect the traffic to an external site as well.
Cookie Based Session Affinity :
If we want to keep user sessions on the same server then Cookie Based Session Affinity is a very helpful feature. If we activate Cookie Based Session Affinity feature, the application gateway will redirect all the subsequent requests/traffic from a particular user session to the same server for processing on which the user was started. This feature is optional and can be configured later if required.
SSL Termination :
In application gateway SSL termination can be done in a different device other than the webserver. It allows communication with backend instances un-encrypted. SSL Termination at application gateway, remove the encryption and decryption overhead from the webserver. So the processing time becomes faster and the response time is less. It isn’t always acceptable by the business, so there is also an option for end-to-end SSL communication. SSL termination allows servers to handle a large volume of simultaneous connections, or sessions, and cookies.
SSL termination, a form of SSL Offloading. SSL offloading is the process of removing the SSL-based encryption from incoming traffic that a web server receives to relieve it from the decryption of data. Security Socket Layer (SSL) is a protocol that ensures the security of HTTP traffic and HTTP requests on the internet. (From MS Doc)
Custom Error Page :
Application gateway can display a custom error page when a request can’t reach the backend. If an error is raised from the backend servers, then a custom error page can be displayed.
Custom error pages are supported for the following two scenarios.
1) Maintenance page
2) Unauthorized access page
Custom error pages can be defined at the Global level and at the Listener level. At the global level, the error page applies to traffic for all the Web applications deployed on that application gateway. Creating global level custom error pages from the Azure portal is currently not supported but we can use Azure PowerShell to configure a global custom error page.
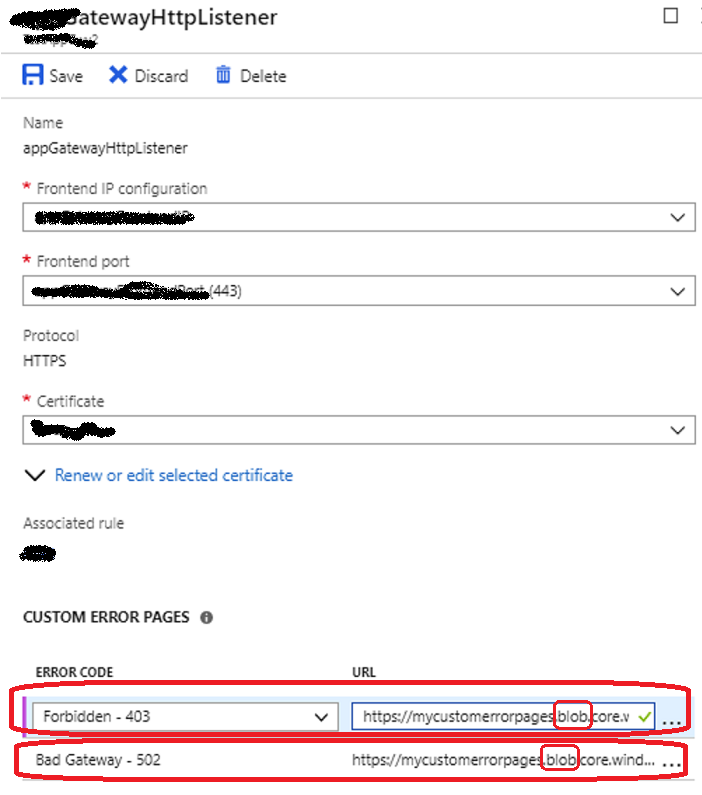
Figure 4: Azure AG – URL Based Routing
Multi-Site Hosting :
This Multi-Site Hosting feature of the application gateway allows us to configure more than one website on the same application gateway instance. It helps to configure a more efficient topology for our deployment by adding up to 100 websites for one application gateway. So we can add up to 100 listeners to handle those 100 websites. each website can have its own back-end pool.
Rewrite HTTP Headers :
Application Gateway also provides a feature Rewrite HTTP headers. HTTP headers allow a client and server to pass additional information with requests or responses. This feature allows us to add, remove, or update HTTP request and response headers while the request and response packets move between the client and backend pools. We can also add conditions, to ensure that the specified headers are rewritten only when certain conditions are met. An application gateway inserts four additional headers to all requests before it forwards the requests to the backend. These headers are x-forwarded-for, x-forwarded-proto, x-forwarded-port, and x-original-host. The format for an x-forwarded-for header is a comma-separated list of IP: port. If session affinity is enabled as an option, then it adds a gateway-managed affinity cookie (Referenced from MS Doc). Please check this link, if you want to know more about HTTP Header Rewrite.
Web-socket and HTTP/2 Traffic :
WebSockets/ HTTP 2.0 provide a persistent connection between a client and server that both parties can use to start sending data at any time. Client and Server communicate over that same TCP connection for the life-cycle of WebSocket connection. A server can push information to the client (which does not allow direct HTTP).
I hope this article gives a basic understanding of Application Gateway features. My next article of this series is EP7 – Create An Application Gateway With URL-Based Routing Configuration- 1.
Thanks for reading 🙂
Keep reading, share your thoughts, experiences. Feel free to contact us to discuss more. If you have any suggestions/feedback/doubts, you are most welcome.
Stay tuned on the blog, will come up with more such articles.
Manas KJ




